
THE FASCINATING WORLD OF NETWORKING
OPTIMIZED FOR GOOGLE CHROME
PART IV: Client-based SSL VPN using ASDM
If Network Address Translation (NAT) is configured on the ASA, a NAT exemption rule must be created for the configured IP address pool. Like IPsec, SSL client address pools must be exempt from the NAT process because NAT translation occurs before encryption functions.
Check the Exempt VPN Traffic from Network Address Translation check box, and then click Next .
Click Next and an information screen on how to launch AnyConnect will open.

Click Next again and the VPN Wizard displays a summary of the configured selection, as shown in Figure.
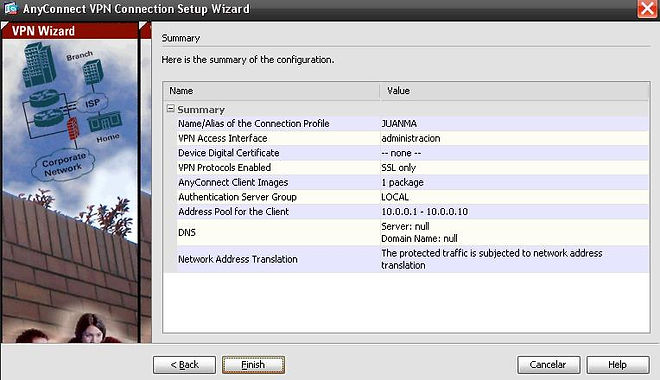
Review the information displayed. If correct, click Finish . Otherwise, click Back and correct the misconfiguration.
The configuration is then committed to the ASA, and the AnyConnect Connection Profiles screen opens, as in Figure.

I want to download the Cisco AnyConnect client from a browser, so Click on Enable “Cisco AnyConnect…”, select outside interface (Administracion in my GNS3 example), Allow Access and Enable DTLS in SSL Access and Apply .
From this screen, you can specify enable client access on the interfaces you select, and you can select, add, edit, and delete connections (tunnel groups). You can also specify whether you want to allow a user to select a particular connection at login.
To verify the configuration, you must do the following from a remote host:
1. Open a web browser and enter the login URL for the SSL VPN into the Address field.
2. If the ASA requests confirmation that this is a trusted site, accept and proceed. The ASA performs a series of compliance checks, platform detection, and finally selects/downloads the software package. A security warning displays if AnyConnect must be installed. If the AnyConnect Client must be downloaded, ActiveX must be installed and configured to trust the ASA. It is important that the security appliance is added as a trusted network site. After the client completes the autodownload, the web session automatically launches the Cisco AnyConnect SSL VPN Client.
Login from the Remote Host
Open web browser and enter the login URL for the SSL VPN into the address field.

-
The ASA may request confirmation that this is a trusted site.
-
If requested, click Yes to proceed.
-
-
The ASA performs a series of compliance checks, platform detection, finally selects / downloads the software package.

In my GNS3 example:

Click in the link. You have to download and install the file anyconnect:
